Did you ever wonder what happens when a cybersecurity company becomes a tool for spreading malware? This is exactly what happened to the cybersecurity company Cyberhaven last Wednesday, leading to the infection of its 400,000 users with malicious code through a Chrome extension.

Cyberhaven is one of the startups in the DLP (Data Loss Prevention) space — a tool designed to prevent sensitive organizational data from leaking. They offer a Chrome extension which blocks users from entering sensitive organizational information into unauthorized platforms like ChatGPT or Facebook. Recently, the company has been thriving, raising $88 million in its latest funding round.
Hour by hour, what happened?
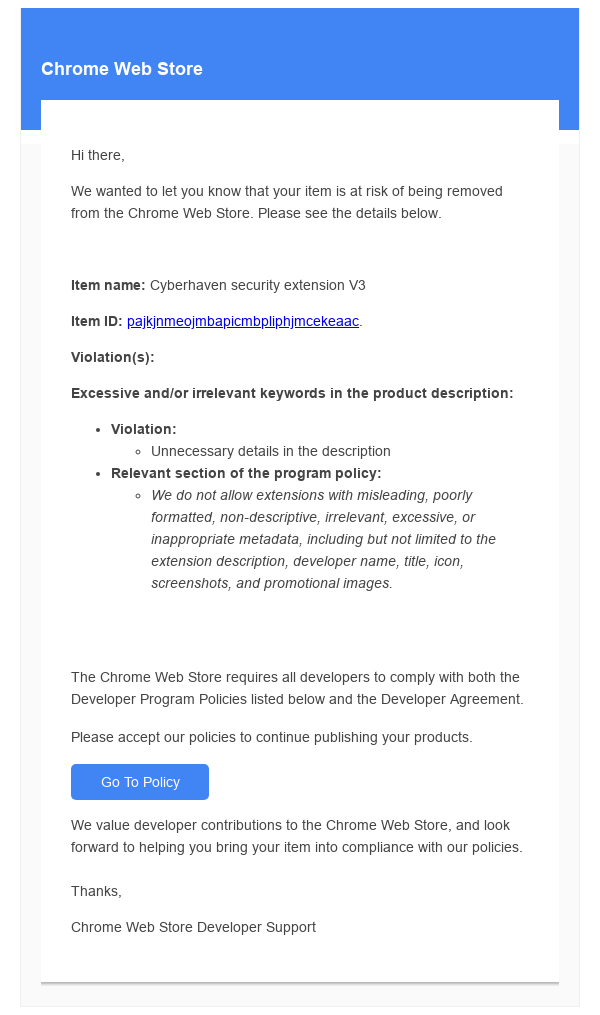
On Tuesday evening, Christmas Eve, Cyberhaven’s admin received a troubling email — stating that their Chrome extension was violating Google’s policies and was at risk of being removed from the Chrome Web Store. For a company like Cyberhaven, such removal would be a devastating blow. However, the email was nothing more than a phishing campaign designed to trick the admin into falling for the scam.
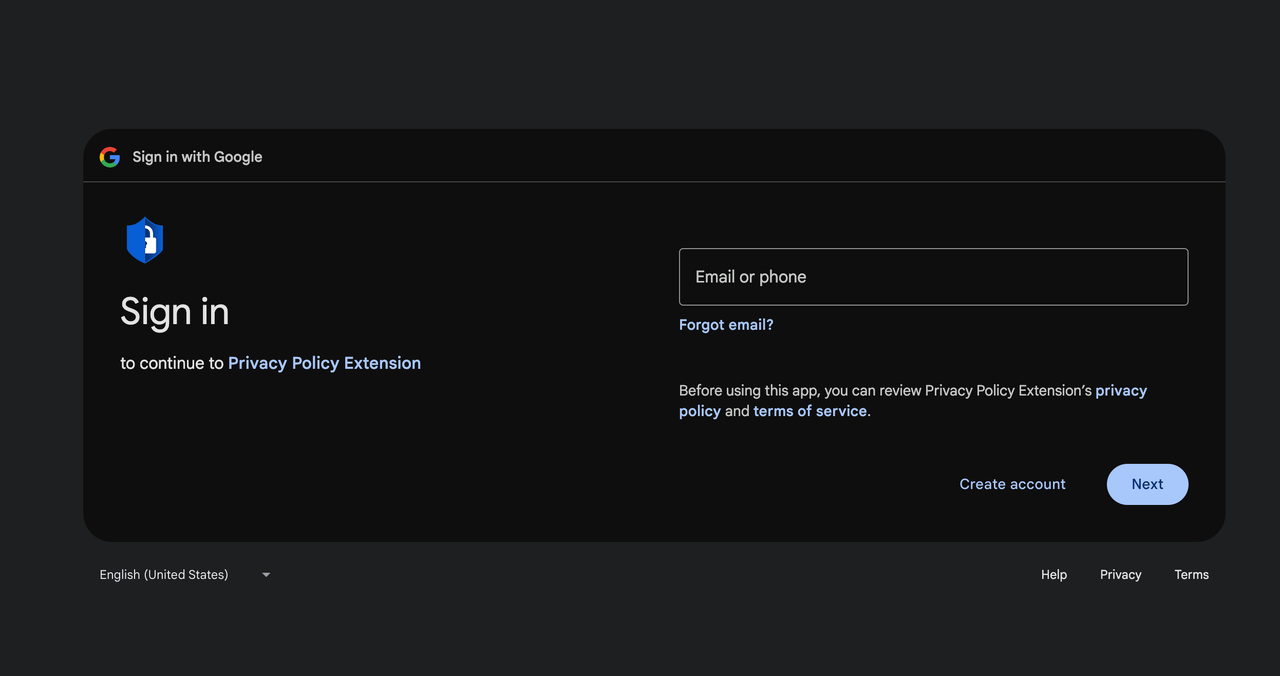
Clicking on the email led the admin to a Google consent screen, requesting permission for an OAuth application named Privacy Policy Extension. This application was actually a tool controlled by the attacker. By granting permission, the admin unknowingly gave the attacker the ability to upload new versions of Cyberhaven’s Chrome extension to the Web Store.
Once the attacker gained access to upload new extension updates, they released a malicious version of Cyberhaven’s Chrome extension. Even though Google claims to perform security checks and scans for every new version uploaded to the store, the new version including the malicious code was published shortly after, on Wednesday morning (December 25th, 2024).
It’s important to understand that browser extensions update automatically. This means that as soon as the malicious version was published, it was pushed to nearly all 400,000 Cyberhaven users. Pretty bad.
What did the malicious code do?
Analysis revealed that it was designed to steal users’ passwords, cookies, and other information that could enable account takeovers.
Several hours after the malicious version was published, Cyberhaven’s security team identified the attack and acted to remove the malicious code. On Friday, the company issued a statement about the breach, which sent shockwaves through the cybersecurity industry. But the story doesn’t end there. Following the announcement, further research unearthed tens of popular extensions containing the same malicious code. It appears that the same campaign also successfully targeted developers of other Chrome extensions.
Currently, it’s estimated that over a million computers have been infected by the malicious code through extensions like VPNCity, Reader Mode, and others. The investigation is still ongoing, but so far there has been a total of 16 Chrome extensions found so far similarly compromised. IOCs attached at the bottom of the blog post.
What can you do about it?
Firstly we highly recommend ensuring your environment has not been infected, you can leverage the IOCs mentioned below or contact us at ExtensionTotal. Additionally, the way to ensure this does not happen in your organization is to implement Version Pinning. Version pinning basically means pinning pre-approved versions of extensions in your organization, so you are not prone to malicious automatic update attacks. This can be done by using a product like ExtensionTotal Enterprise.
Even when we trust the developer of an extension, it’s crucial to remember that every version could be entirely different from the previous one. If the extension developer is compromised, the users are effectively compromised as well — almost instantly.
Additionally, these types of attacks happen in many similar software ecosystems, as observed by ExtensionTotal, for example in other browser extensions (Edge, Safari, Firefox), IDE extensions (Visual Studio Code, JetBrains), and code packages (NPM, Pypi).
This is a classic problem with software supply chain that we meet every day in large enterprises, how do you balance security and productivity? We’ve built ExtensionTotal to do just that, for practitioners and enterprises alike.
Trusted by Fortune 100s, 500s, and defense tech enterprises, ExtensionTotal automates security processes, providing visibility, governance, and proactive risk to reduce and balance this attack surface.
If you’d like to chat, hit us up here 🤙
*** UPDATE 30/12/2024 13:03 UTC ***
ExtensionTotal has uncovered 3 more malicious Chrome extensions with 120,000 users as part of the same campaign, the investigation is still ongoing.
*** UPDATE 31/12/2024 6:13 UTC ***
Many additional compromised Chrome extensions which contain malicious code were found, we recommend staying updated through the incident page.
from ExtensionTotal, much of the blog post is inspired by his LinkedIn post.